- What is Cloud Vulnerability Assessment?
- Importance of Cloud Vulnerability Assessment?
- How to perform Cloud Vulnerability Assessment?
- How to improve the Cloud Vulnerability Assessment process?
- Cloud Vulnerability Assessment challenges
- Why should you go for a managed service company with SecOps expertise like DiscoverCloud?
- The bottom line
Companies across the world are in a race to adopt cloud computing effectively, and that’s not surprising! Cloud computing is highly scalable, flexible, and cost-effective, with proven benefits for all types and sizes of businesses. But there’s a catch! With all their benefits, cloud environments also come with the risks of data breaches, financial losses, damaged reputation, and regulatory fines if their safety is compromised.
In fact, VentureBeat reported that 81% of organizations experienced a public cloud-related security incident in 2021, and 45% had to deal with four or more incidents. Now that’s a worrying statistic!
However, these risks can be avoided by proactive and regular cloud vulnerability assessments. These are essentially “health check-ups” for a company’s cloud environment that help identify and fix any threats before they spiral out of control. In this article, we will learn more about cloud vulnerability assessment and its implementation to help you leverage the benefits of the cloud safely. Let’s begin!
What is Cloud Vulnerability Assessment?
A cloud vulnerability assessment is a process of scanning and testing cloud resources, such as applications, servers, databases, storage buckets, and network configurations, for security weaknesses and misconfigurations that could be exploited by malicious actors.
It is aimed at discovering vulnerabilities in your cloud infrastructure, such as outdated software, insecure protocols, open ports, weak encryption, default credentials, excessive permissions, and exposed data. The assessment also helps you detect and solve non-compliance with industry standards and regulations, such as PCI DSS, HIPAA, GDPR, and NIST.
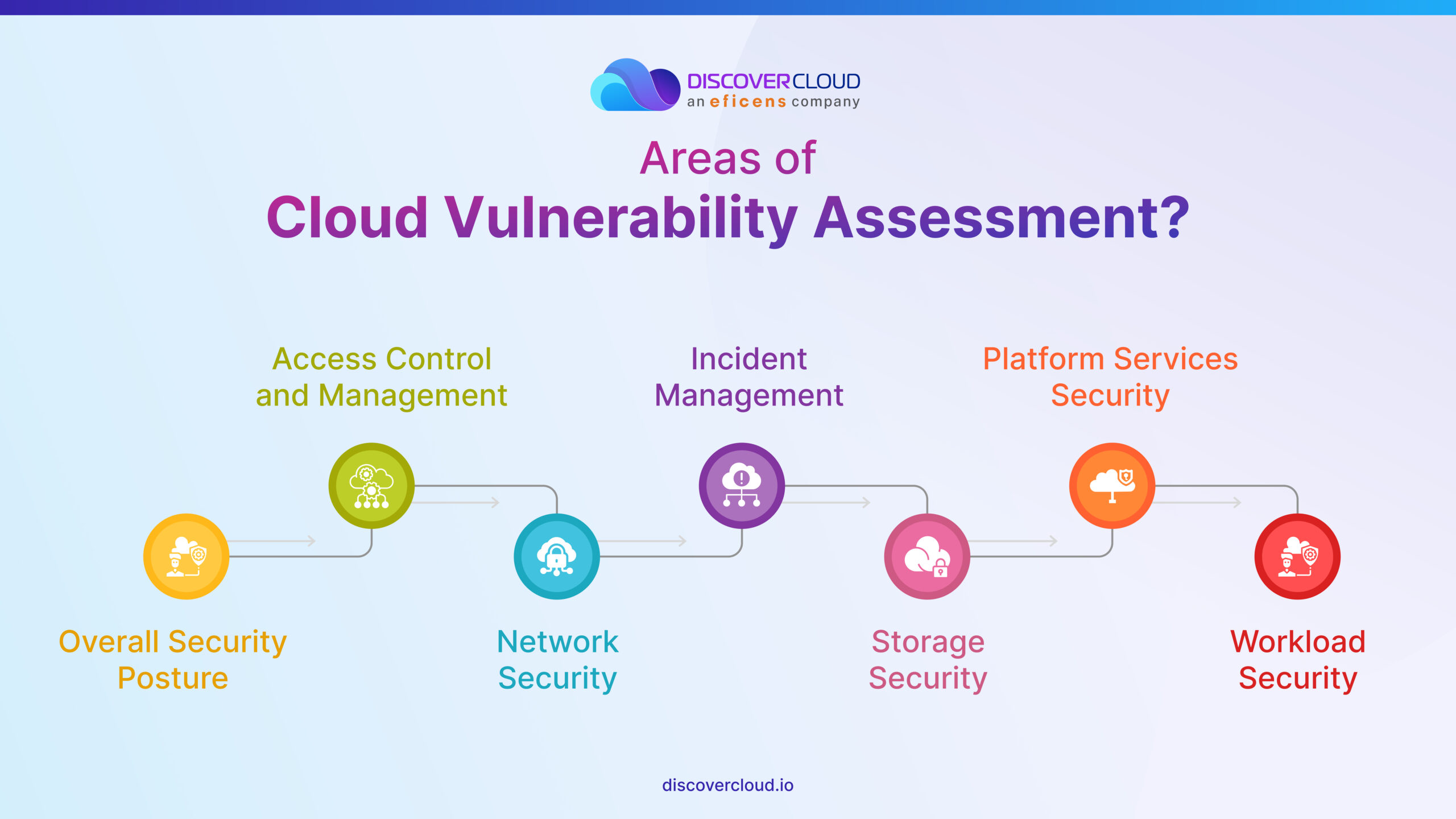
A cloud vulnerability assessment typically focuses on seven areas, which include overall security posture, access control and management, network security, incident management, storage security, platform services security, and workload security.
Importance of Cloud Vulnerability Assessment?
A cloud vulnerability assessment is an invaluable tool that can seriously boost an organization’s security while also serving as a testament to its commitment to maintaining high-security standards. Here are some specific reasons that make cloud vulnerability assessment essential in today’s cybersecurity landscape:
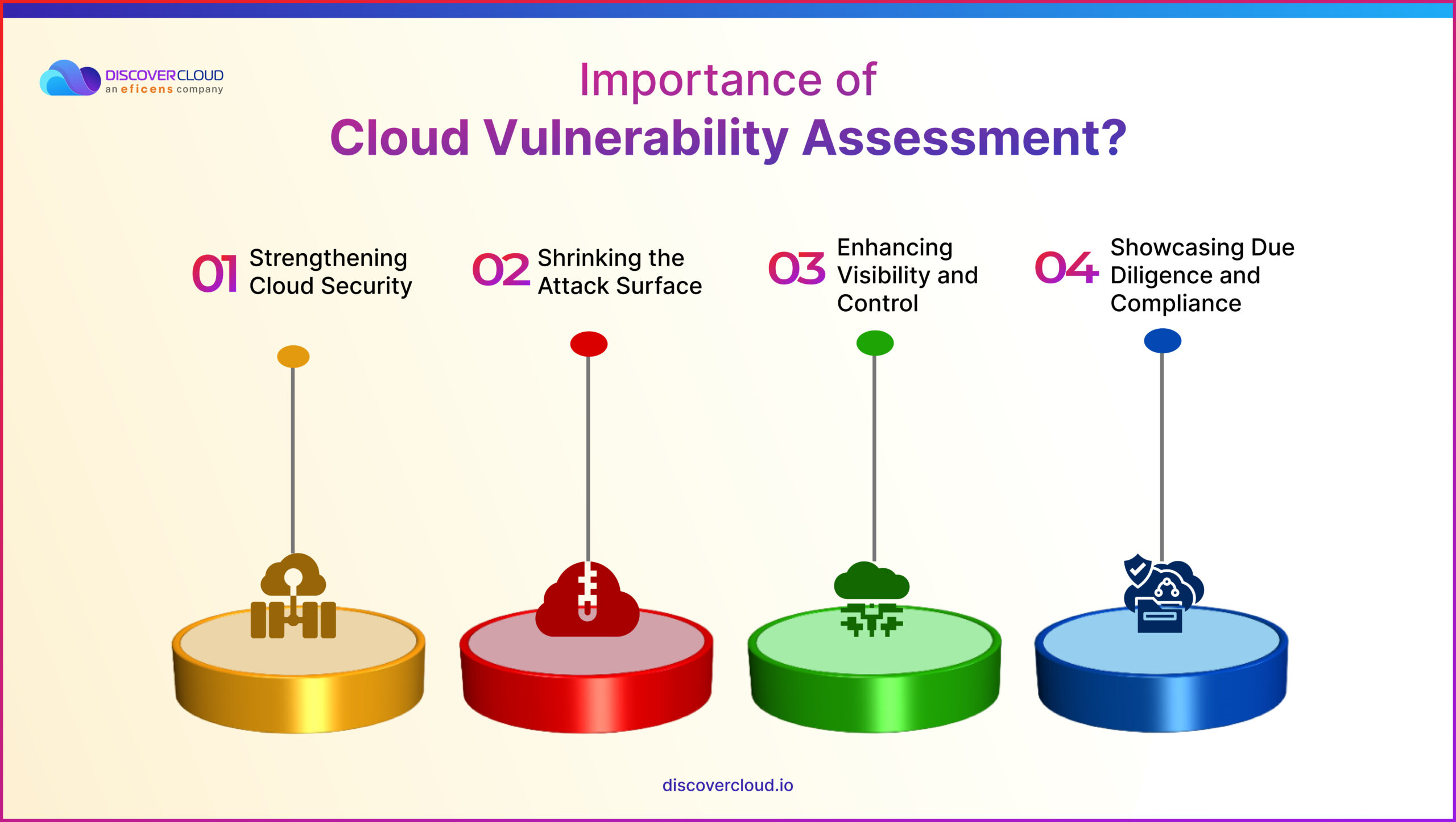
Strengthening Cloud Security
The first and foremost reason is that it boosts an organization’s cloud security. It does this by pinpointing and ranking the most severe and pressing vulnerabilities that need immediate attention. So, it’s like a roadmap, guiding you and your team on what security issues to tackle first, helping you to fortify your defenses effectively.
Shrinking the Attack Surface
Secondly, a cloud vulnerability assessment could dramatically reduce an organization’s attack surface. It’s similar to sealing off weak spots in a fortress before an enemy onslaught. By identifying and helping fix potential security loopholes, the assessment keeps the cyber troublemakers at bay.
Enhancing Visibility and Control
Additionally, this assessment offers organizations improved visibility of and control over their cloud sources. Consider it as a detailed inventory check and status report on the organization’s cloud resources. By knowing what’s in the system, one can monitor and manage these resources more effectively.
Showcasing Due Diligence and Compliance
Lastly, undergoing a cloud vulnerability assessment shows that an organization is diligent about upholding security standards. This activity can present solid proof of your organization’s security efforts, something incredibly valuable when faced with regulations and laws related to data security. So, it’s not just about keeping your digital estate secure but also about confidently demonstrating your compliance, which could be vital when dealing with relevant authorities or clients.
Given its importance and growing cybersecurity threats, it is now critical to conduct regular cloud vulnerability assessments for your organization. If you find the process cumbersome, you can also take the help of an agency that has expertise in SecOps, such as DiscoverCloud.
How to perform Cloud Vulnerability Assessment?
A cloud vulnerability assessment is a process that can be performed in different ways depending on the scope, complexity, and frequency of the assessment. Let’s explore the general process in chronological order-
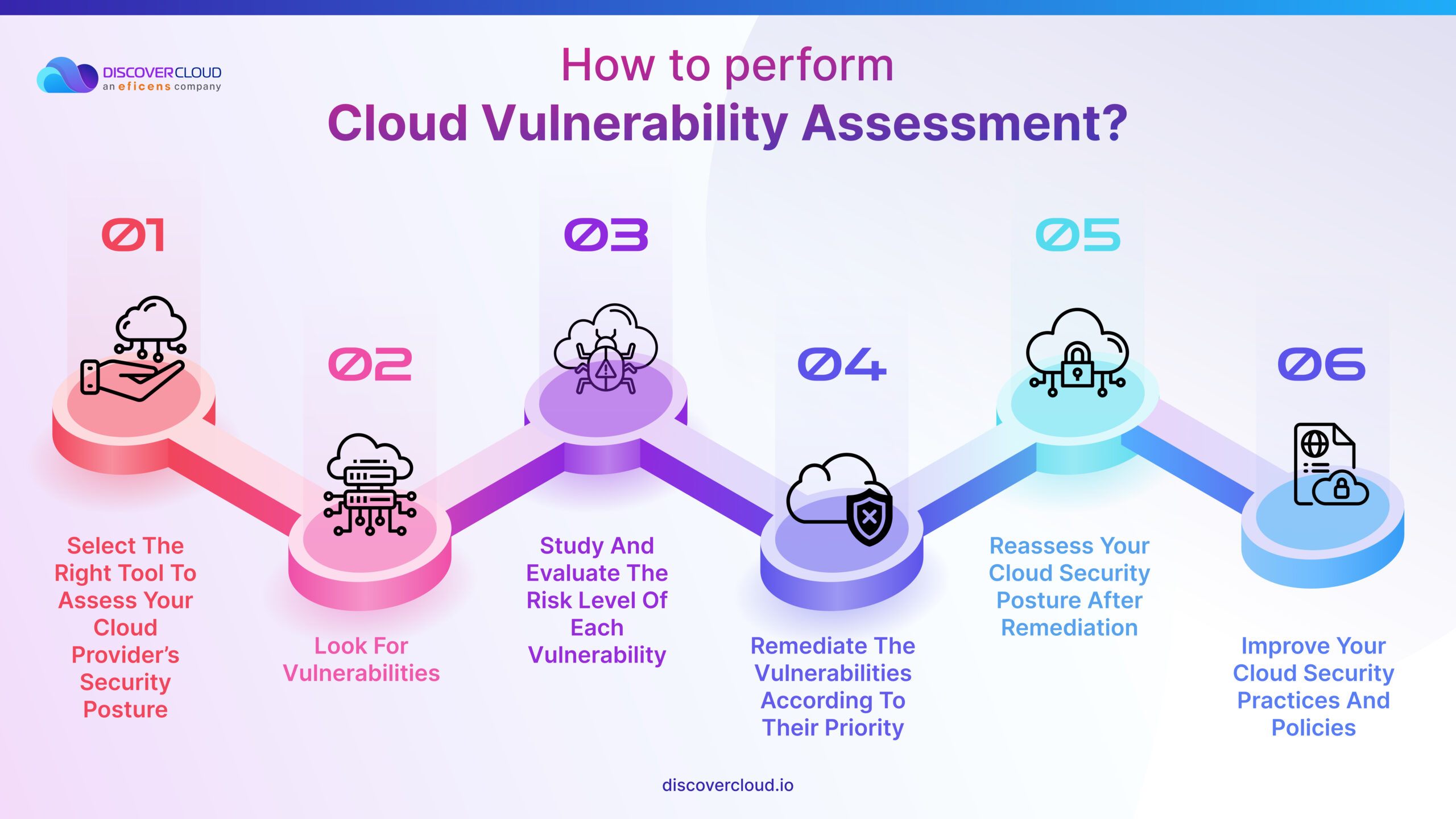
Select the right tool to assess your cloud provider’s security posture
You can use your cloud provider’s native tools, cloud-agnostic tools, or other third-party tools to scan your cloud environment for vulnerabilities and misconfigurations. You can also hire experts or expert agencies like DiscoverCloud at the onset if you lack the time or expertise, and they will do all the hard work!
Look for vulnerabilities
Now, you must review the basic security features and policies offered by your cloud service provider (CSP), such as AWS, GCP, or Azure. Check the cloud configuration settings, policies, logs, and reports to identify any anomalies or deviations from the best practices. You can do this manually using experts or use tools or scripts to scan and test the cloud resources for known vulnerabilities and misconfigurations. You can also go for a hybrid approach that leverages both manual and automated assessments for a more comprehensive overview. In any case, remember to include these aspects-
- Overall security posture- Conduct interviews, scrutinize documentation, and gain a complete understanding of your current security infrastructure.
- Access control and management- Review the identity and access management, user accounts, and roles for each member of your squad.
- Network security- Check the segmentation and firewall policies against common misconfigurations.
- Incident management- Review the incident response policy related to cloud infrastructure, including roles and processes related to an incident.
- Storage security- Assess the state of your storage systems, from object-level to block-level storage, and even related snapshots.
- Platform services security- Understand the security configuration of advanced services offered by your service provider to enjoy their benefits safely.
- Workload security- Assess the security for workloads encompassing virtualized servers, functions, server-hosted containers, and serverless containerized workloads.
Study and evaluate the risk level of each vulnerability
Once you have found the weak points, you must analyze the impact and likelihood of each vulnerability being exploited by an attacker. You can use a risk matrix or a scoring system, such as CVSS, to prioritize the most critical vulnerabilities that need immediate attention.
Remediate the vulnerabilities according to their priority
You should now implement the appropriate mitigation or patching strategies to fix the vulnerabilities or reduce their impact. You can use automation tools or scripts to speed up the remediation process and ensure consistency or let the experts handle it, in case you hired an expert agency. Remember to involve your DevOps and development teams at this step to ensure that the remediation does not affect the functionality or performance of your cloud applications.
Reassess your cloud security posture after remediation
It’s time to verify that the remediation actions have successfully resolved the vulnerabilities and improved your cloud security posture. You can use the same tools or methods that you used in the first two steps to scan your cloud environment again and compare the results.
Improve your cloud security practices and policies
You must learn from the results of your cloud vulnerability assessment and identify the root causes of the vulnerabilities. Accordingly, remember to update your cloud security policies and best practices to prevent similar vulnerabilities from occurring in the future.
If you are wondering how frequently you should conduct this assessment, there is no fixed answer. The frequency of cloud vulnerability assessments depends on several factors, such as the size, complexity, and sensitivity of the cloud environment, the level of risk tolerance, the rate of change, and the regulatory requirements.
Generally, organizations should conduct cloud vulnerability assessments at least once a year or whenever there are significant changes in the cloud environment or the threat landscape. If you find this too expensive or difficult, you can also go with an expert like DiscoverCloud. But remember to conduct regular assessments in any case to avoid growing cyber threats.
How to improve the Cloud Vulnerability Assessment process?
Some of the ways organizations can improve their cloud vulnerability assessment process to improve its effectiveness are:
Aligning Assessment with Business Objectives and Risk Appetite
Make sure your vulnerability assessment is relevant and aligned with your organization’s goals, priorities, and risk tolerance. By aligning the process with your corporate objectives and risk appetite, your cloud security efforts become more focused and strategically effective.
Adopting a Holistic and Integrated Approach
Consider all aspects of your cloud environment—people, processes, technology, and data—when conducting your assessment. By integrating these dimensions into a comprehensive and consistent framework, you can gain a more accurate understanding of your cloud environment’s vulnerabilities and improve your overall security posture.
Leveraging Best Practices and Standards
Follow established guidelines and recommendations from reputable sources, such as industry associations, regulatory bodies, and security experts, when conducting your assessments. These time-tested practices and standards will help you carry out effective and efficient vulnerability assessments, contributing to a more secure cloud environment.
Reviewing and Updating Regularly
Continually evaluate and measure your assessment’s performance and outcomes. Make necessary adjustments or improvements based on feedback or changes in your organization’s environment. An up-to-date vulnerability assessment process will address new vulnerabilities and threats, ensuring that your cloud security remains strong and relevant to evolving challenges.
Streamlining the Process Through Automation
Imagine being able to simplify and accelerate your cloud vulnerability assessment process with the help of automation tools and techniques. This valuable approach enables more frequent, consistent, and accurate scanning of your cloud environment. By reducing the likelihood of human errors and conserving time and resources, automation enables faster, more efficient remediation of vulnerabilities—ultimately boosting your cloud security posture.
Educating and Training Your Staff
Envision a team that’s fully aware of the importance and benefits of cloud vulnerability assessments because they’ve received proper training and guidance on conducting these assessments securely. By educating your staff and fostering a culture of security awareness and responsibility, your organization becomes more capable of countering cloud vulnerabilities and threats effectively.
Partnering with the Right SecOps Expert Agency for Success
If you need external assistance or expertise for your cloud vulnerability assessment process, consider working with a reputable and reliable SecOps expert agency like DiscoverCloud that offers top-notch cloud services and solutions. Such an agency will help you design, implement, and manage your cloud vulnerability assessment process with ease, leveraging their years of experience and skills in the security and operations domains. A SecOps expert agency will also help integrate your security and operations teams, fostering better collaboration that leads to improved cloud security outcomes.
Cloud Vulnerability Assessment challenges
Cloud vulnerability assessment is a complex and time-taking process that poses many challenges, especially for businesses that lack expertise in the area. Some of the challenges faced during cloud vulnerability assessment are:
False positives or negatives
These are errors or inaccuracies in the results of the assessment that may indicate a vulnerability that does not exist or miss a vulnerability that does exist. These errors can affect the reliability and validity of the assessment and lead to wasted time or resources or increased risk exposure.
Scope and Coverage
These are issues related to defining and determining what to include or exclude in the assessment. These issues can affect the completeness and comprehensiveness of the assessment and lead to gaps or overlaps in the security coverage.
Lack of Expertise
A significant percentage of companies also struggle because they feel their IT and business managers lack the knowledge and experience necessary to handle the demands of cloud computing.
Cost and Complexity
Cost and complexity are factors related to the resources and efforts required to conduct and maintain the assessment. They can affect the feasibility and sustainability of the assessment and lead to trade-offs or compromises in the security quality.
Why should you go for a managed service company with SecOps expertise like DiscoverCloud?
As we discussed, SecOps experts are armed with practical risk reduction and risk assessment strategies and tools, and these simplify the entire assessment process while helping you tackle the discussed challenges efficiently. However, not all experts have the advanced tools, fast results, and vast experience that DiscoverCloud offers!
At DiscoverCloud, we offer accelerators on our free online portal that instantly analyze your cloud environment and provide detailed insights. Moreover, our experts leverage their expertise in cloud security along with the accelerators to provide actionable advice and support tailored to your business.
Our advanced accelerators combined with our decades of experience culminate into the perfect DiscoverCloud managed service and SecOps solutions for all businesses to secure their cloud environments.
What’s more? Our approach to SecOps is not just limited to protecting your assets. It’s about creating a monitored and streamlined cloud environment where security and IT operations teams work in unison to spot, communicate, and address potential security risks timely.
The bottom line
While cloud computing is an awesome asset, remember – with great power comes great responsibility! Keep an eye on your cloud security with regular cloud vulnerability assessments to enjoy its benefits without the risks. Don’t hesitate to leverage the services of a cloud managed service company for assistance with your cloud vulnerability assessment and remediation. All the best!