If you’ve ever felt overwhelmed by the complexities of cloud security, you’re not alone! With 45% of breaches being cloud-based and a staggering 80% of companies experiencing at least one cloud security incident in the past year, the need for robust vulnerability management in the cloud has never been more pressing. Whether you’re steering a startup or navigating a multinational corporation, the stark reality is that cloud vulnerabilities can compromise not just your data but also your operational integrity and customer trust.
So, understanding and effectively managing these vulnerabilities is a crucial aspect of your business’s cybersecurity strategy. As we delve into the world of cloud security, we’ll uncover why vulnerability assessment in the cloud is not just a preventative measure but an indispensable tool in your digital arsenal.
Let’s embark on a journey to decode the best practices in vulnerability management, ensuring that your venture in the cloud is both secure and successful.
Why is Cloud Vulnerability Management Important?
In today’s interconnected business world where cloud computing is a necessity, vulnerability management in the cloud emerges as a pivotal component of cybersecurity. It’s a stark reality that a breach in cloud security can have far-reaching impacts on your business, from financial losses to reputational damage.
Cloud vulnerability management is a continuous process of identifying, reporting, and remediating security risks within cloud platforms. It ensures that your cloud environment is not just a repository of data but a fortress safeguarding your digital assets. Vulnerability management in the cloud is not just about reacting to threats but about proactively identifying and mitigating potential risks before they can be exploited.
In addition to it being cost-effective, as it reduces the expenses associated with fixing vulnerabilities post-breach, this approach is also a time-saver as it prevents organizations from expending valuable resources on aftermath management.
At DiscoverCloud, our expertise in vulnerability assessment in the cloud and management forms a crucial part of our commitment to safeguarding your digital assets and enhancing your cloud journey.
Cloud-based Vulnerabilities to Look Out For
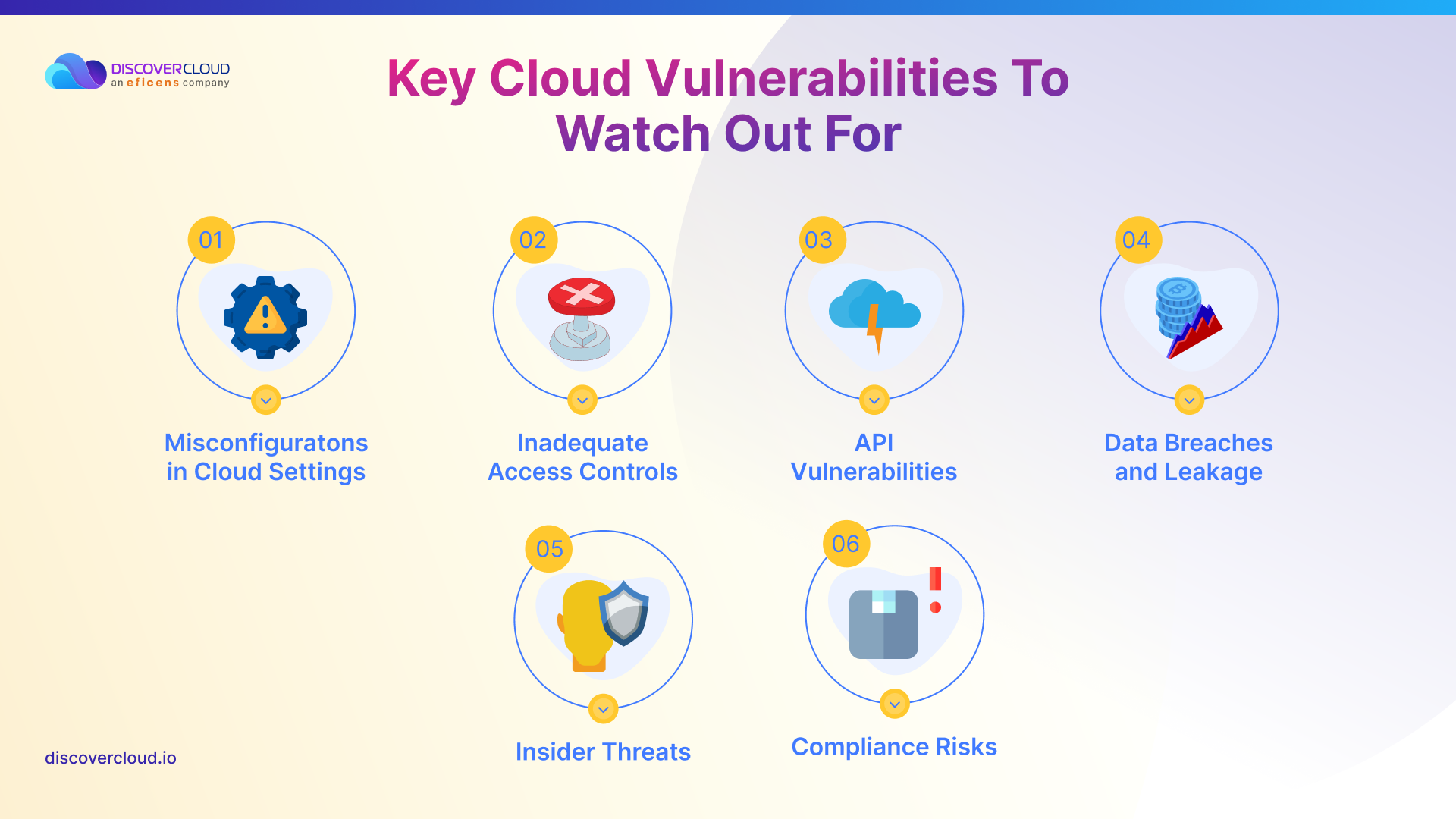
When it comes to cloud computing, numerous vulnerabilities might be lurking around, often hidden in plain sight. Recognizing these vulnerabilities is the first step in fortifying your cloud infrastructure against potential threats. Here, we outline some of the most common cloud-based vulnerabilities that businesses should be vigilant about.
- Misconfigurations in Cloud Settings- Often overlooked, misconfigurations in cloud settings are a leading cause of security breaches. Simple errors in setting up cloud environments can leave your data exposed to unauthorized access. Regular audits and checks are essential to ensure that all cloud configurations align with the best security practices.
- Inadequate Access Controls- Cloud environments often suffer from inadequate access controls, which can lead to unauthorized data access. Ensuring strict access controls and employing principles like least privilege can significantly reduce this risk.
- API Vulnerabilities- APIs are integral to cloud services but can also be a weak link if not properly secured. Unsecured APIs can expose your cloud infrastructure to various attacks, making API security a priority in cloud vulnerability management.
- Data Breaches and Leakage- Data stored in the cloud can be susceptible to breaches and leakage. Encryption, both at rest and in transit, along with robust data backup strategies, are crucial in mitigating this risk.
- Insider Threats- Not all threats come from outside; insider threats are a significant concern in cloud security. Continuous monitoring and employing advanced analytics can help in the early detection and prevention of such threats.
- Compliance Risks- Non-compliance with regulatory standards can lead to vulnerabilities in the cloud. It’s vital to continuously review and update cloud practices to stay in line with evolving compliance requirements.
By understanding and actively monitoring these vulnerabilities, businesses can significantly enhance their cloud security posture. At DiscoverCloud, our suite of services, including cloud infrastructure management and cloud mitigation strategies, is designed to help you identify and address these vulnerabilities, ensuring a secure and resilient cloud environment for your business.
Best Practices for Vulnerability Assessment in Cloud
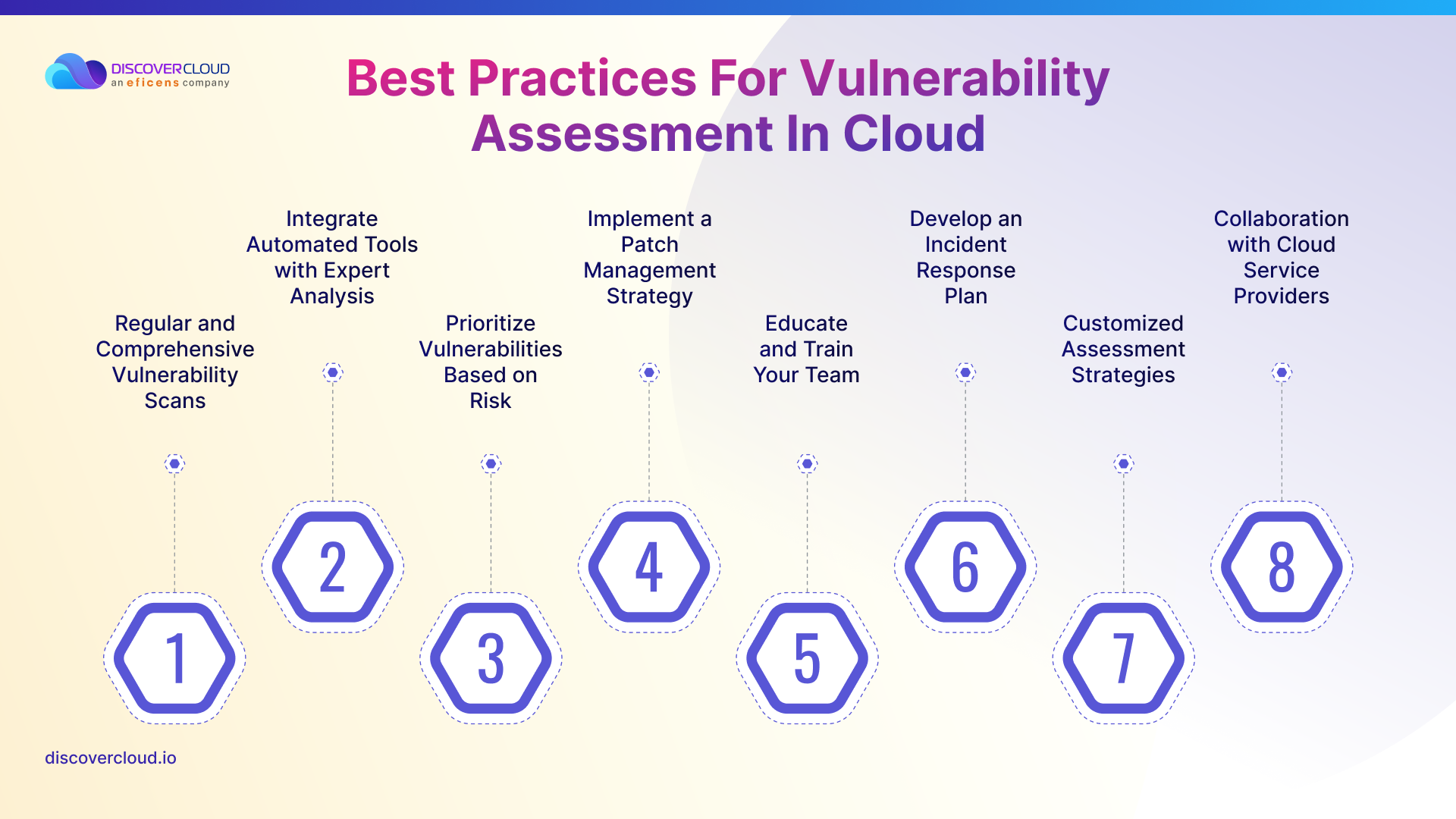
Conducting thorough and regular vulnerability assessments is paramount for securing cloud infrastructures. Here, we outline some best practices that can enhance the effectiveness of your vulnerability assessment in the cloud:
- Regular and Comprehensive Vulnerability Scans- Consistency is key. Conduct regular vulnerability scans to identify potential security gaps in your cloud infrastructure. Ensure that these scans are comprehensive, covering all aspects of your cloud environment.
- Integrate Automated Tools with Expert Analysis- While automated tools are efficient in identifying vulnerabilities, human expertise is crucial for accurate analysis and interpretation of the findings. Combining automated vulnerability assessment tools with expert analysis ensures a more effective identification and mitigation strategy.
- Prioritize Vulnerabilities Based on Risk- Not all vulnerabilities pose the same level of risk. It’s important to prioritize them based on the potential impact on your business. Addressing high-risk vulnerabilities first can significantly reduce the likelihood of a major security incident.
- Implement a Patch Management Strategy- Once vulnerabilities are identified, timely patching is essential. Develop a patch management strategy that includes regular updates and fixes for identified vulnerabilities.
- Educate and Train Your Team- Human error can often lead to vulnerabilities. Educating and training your team on best practices in cloud security and vulnerability management is crucial in minimizing these risks.
- Develop an Incident Response Plan- In case of a security breach, having a well-defined incident response plan can help quickly address the issue and mitigate its impact.
- Customized Assessment Strategies- Recognize that each cloud environment is unique. Tailoring your vulnerability assessment strategies to your specific cloud setup can yield more effective results.
- Prioritizing and Addressing Vulnerabilities- Not all vulnerabilities pose the same level of risk. You should categorize vulnerabilities by their potential impact level and address them strategically, focusing first on those posing the highest risk.
- Keeping Up with Emerging Threats- The cloud security landscape is constantly evolving, so it is crucial to keep abreast of the latest threats and adjust your cloud security assessment strategies.
- Collaboration with Cloud Service Providers- Work closely with your cloud service providers to understand their security protocols and how they align with your organization’s vulnerability assessment strategies.
By adopting these best practices, you can significantly enhance the security of your cloud environment. DiscoverCloud, with our expertise in cloud computing and vulnerability management can help you not only in identifying vulnerabilities but also in implementing effective strategies to manage and mitigate them.
How Can DiscoverCloud Help You Manage Cloud Vulnerabilities?
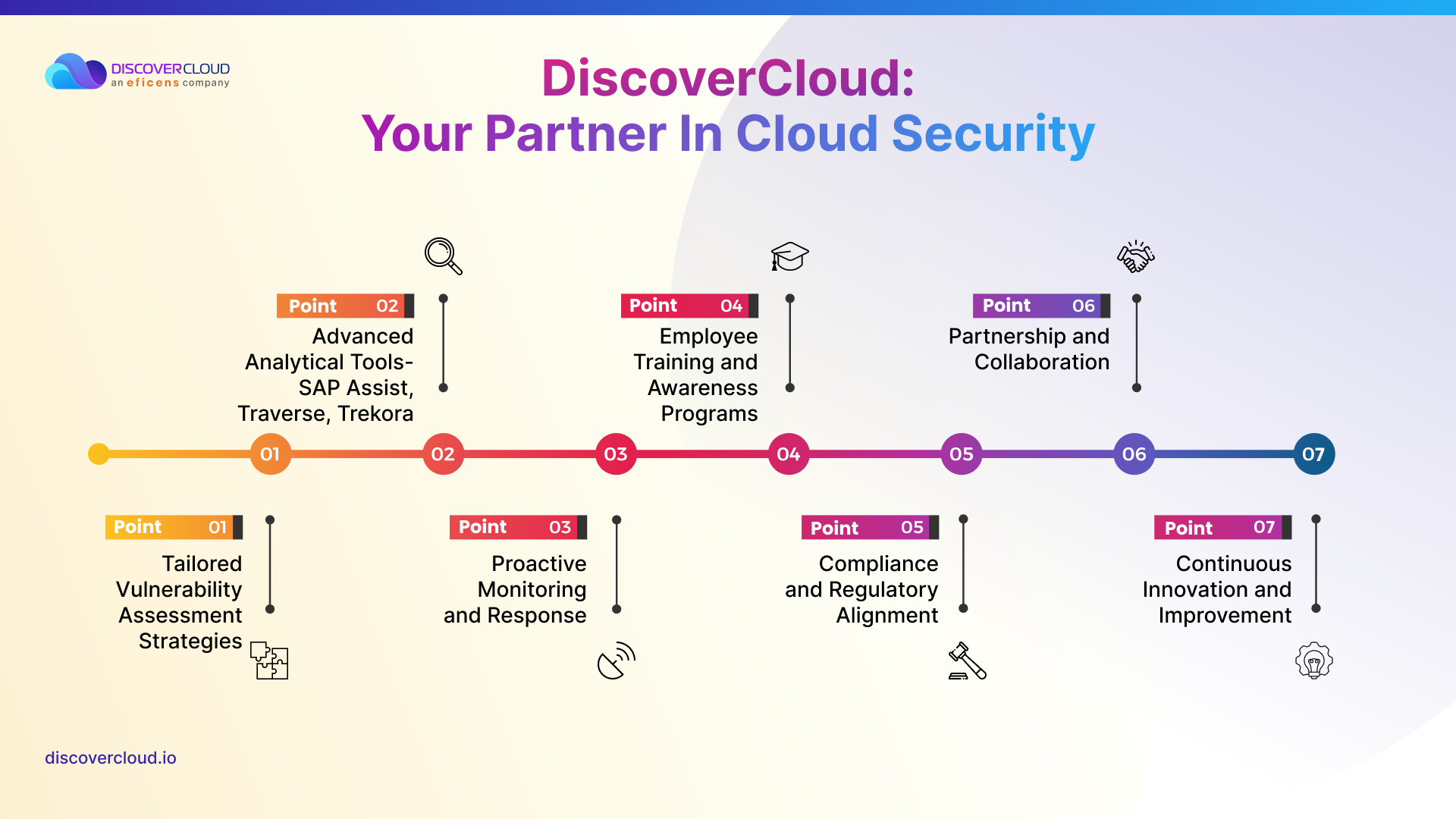
Managing vulnerabilities in your cloud computing operations requires not just tools but a partner who understands the intricacies of your cloud infrastructure. This is where DiscoverCloud steps in as your co-pilot in navigating the complexities of cloud security.
- Tailored Vulnerability Assessment Strategies- At DiscoverCloud, we recognize that each business has unique cloud needs. Our team of experts develops customized vulnerability assessment strategies that align with your specific cloud infrastructure, ensuring a thorough and effective security posture.
- Advanced Analytical Tools- Utilizing our proprietary accelerators, like SAPAssist, Traverse, and Trekora, we provide deep insights into your cloud system. These tools enable us to identify potential vulnerabilities swiftly and accurately, facilitating prompt remediation.
- Proactive Monitoring and Response- Our approach is not just about identifying vulnerabilities; it’s about proactive management. With continuous monitoring and real-time response capabilities, we ensure that any potential threat is addressed before it can impact your business operations.
- Employee Training and Awareness Programs- We extend our expertise beyond technology by providing training and awareness programs. These initiatives are designed to enhance the security acumen of your team, reducing the risk of human error and insider threats.
- Compliance and Regulatory Alignment- Navigating the complexities of compliance can be daunting. Our team stays abreast of the latest regulatory requirements, ensuring that your cloud environment is not only secure but also compliant with industry standards.
- Partnership and Collaboration- We believe in building a partnership with our clients. By working closely with you, we gain an in-depth understanding of your business needs, allowing us to tailor our services for maximum effectiveness.
- Continuous Innovation and Improvement- At DiscoverCloud, innovation is in our DNA. We continuously evolve our methods and tools to stay ahead of emerging threats, ensuring that your cloud infrastructure remains resilient against the ever-changing cybersecurity landscape.
In essence, DiscoverCloud is more than a managed service provider, we are your strategic partner in ensuring a secure, efficient, and compliant cloud environment. With our expertise and tailored solutions, we help you transform cloud vulnerabilities from challenges into opportunities for growth and innovation.
Vulnerability to Victory: Concluding with DiscoverCloud’s Expertise
As we’ve explored in this blog, vulnerability management in the cloud is a fundamental aspect of maintaining a resilient, efficient, and trustworthy digital environment. We also discussed how the right partnership can transform vulnerabilities into strengths, turning potential risks into opportunities for growth and innovation. So, let DiscoverCloud be your guide as you move to a secure, efficient, and future-proof cloud experience!