Let’s face it, cloud computing has skyrocketed over the past decade, emerging as a significant player in the digital ecosystem. Enterprises are placing an increasing reliance on cloud technology. And it’s no surprise, because the versatility, scalability, and improved productivity offered by the cloud are unmatched!
However, businesses are increasingly exposed to numerous digital security threats as they harness the cloud’s capability. Now more than ever, there’s an urgent need for a robust shield to protect your digital realms, and that’s where cloud security assessment comes in.
Want to find more? In this article, we will explore the meaning and importance of cloud security assessment and find out how you can correctly implement it to keep your business safe.
Cloud Security Assessment
Cloud security assessment is your armor on the battlefield of cyberspace. It evaluates your cloud computing environment, helping you identify, understand, and address security vulnerabilities. By exposing potential threats before they become full-blown issues, a cloud security assessment saves you the financial and reputational damage ensuing from data loss or breaches.
An effective cloud security assessment does more than simply identify vulnerabilities. It offers a detailed insight into the security posture of your cloud environment, unearthing areas that could be exploited by an attacker. Moreover, cloud security assessments are not one-and-done procedures. They’re an ongoing process, mirroring the constantly evolving digital threat landscape.
Why is it so important?
“Why should I worry so much about attacks?” you might ask. Well, consider this – Data breaches led to an average of USD 3.92 million in damages in 2019, and the figures have only worsened since. In 2023, IBM found that the global average cost of a data breach peaked at USD 4.45 million, which is a 15% increase over the span of 3 years. Can your enterprise afford to bear such a cost?
More importantly, it’s not just about the financial repercussions. A data breach can inflict severe damage to your brand’s reputation, possibly leading to loss of customer trust, regulatory backlash, and even legal implications in certain scenarios.
A comprehensive cloud security assessment ensures you’re privy to your cloud environment’s real-time state, helping you stay ahead in this digital game of chess. But managing such complex processes in-house could be daunting, and this is where teaming up with seasoned cloud experts like DiscoverCloud can be a game-changer.
Risks and Threats – Avoid the Common Pitfalls
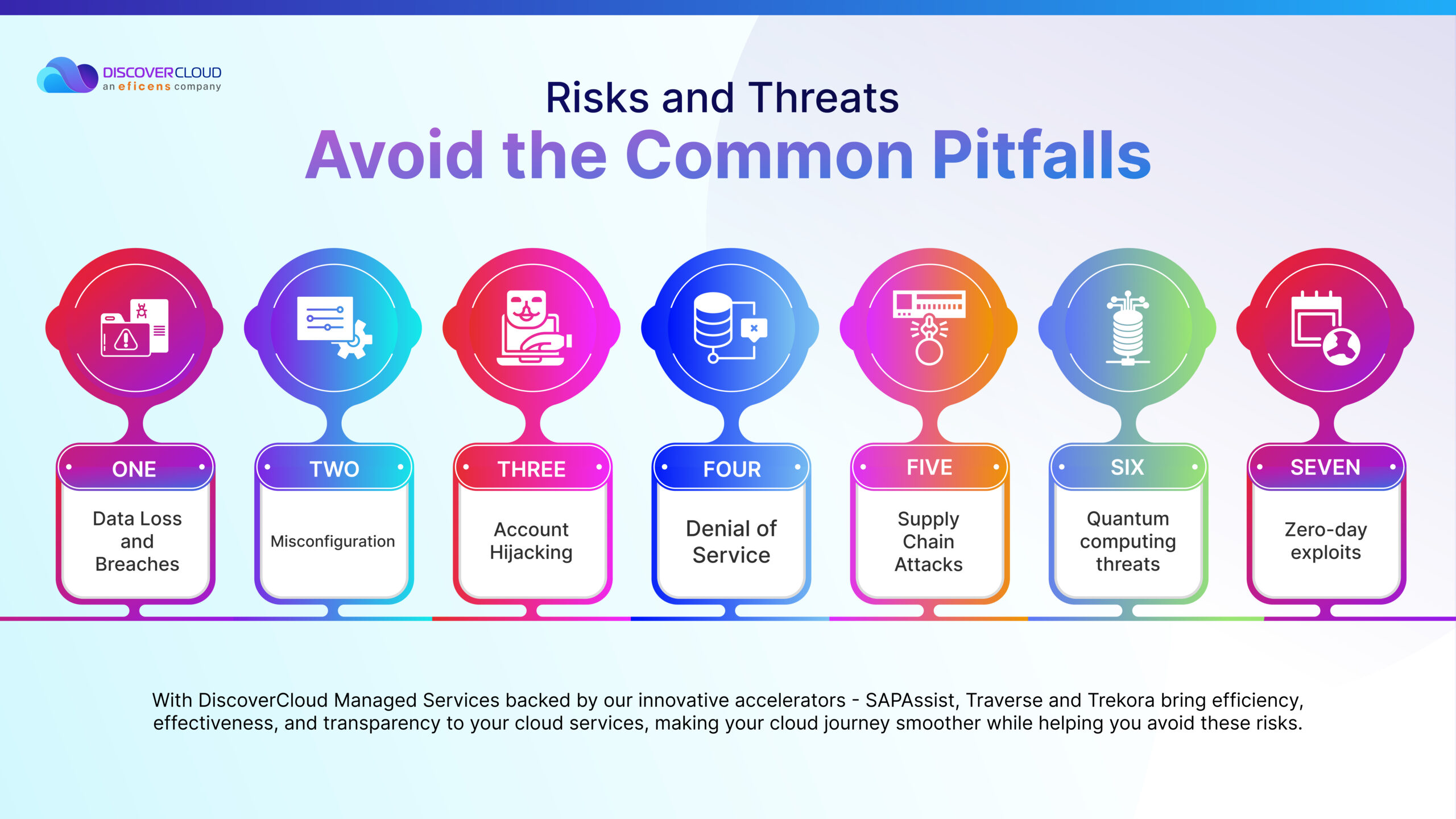
As you move forward on your digital transformation journey, remember – a cloud security assessment is not just important, it’s essential. Here are the key threats and pitfalls that this assessment will help you identify and act against in time-
Data Loss and Breaches
Big data is incredibly valuable but equally vulnerable! A data breach or loss not only erodes your financial resources but also dismantles trust, the cornerstone of any customer relationship. Furthermore, the theft or mishandling of sensitive proprietary information can land you in undesired legal or compliance hurdles. One efficient way to safeguard your data is through early detection and addressing of potential vulnerabilities with innovative tools like Traverse and Trekora, which provide a granular view of your data landscape and finances.
Misconfiguration
Even the tiniest of misconfigurations can inadvertently expose your data or violate critical compliance needs. To avoid such risks, proactive identification and rectification of misconfigurations is critical. Our accelerator, SAP Assist, shines in this instance with its ability to simplify complex SAP migrations and tailor the perfect migration strategy, avoiding any missteps in the process.
Account Hijacking
Account hijacking is the digital equivalent of identity theft. A phishing attack may lead to the loss of vital account credentials, providing unauthorized access to your precious digital resources. The aftermath may range from tampered data to stalled operations to financial losses but can be prevented with the right tools and expertise.
Denial of Service
A denial of service attack is the equivalent of having all entry points to your shop blocked, making you inaccessible to your customers! Imagine the customer dissatisfaction and the subsequent damage to your reputation in such an event. Prevention or early detection is the best line of defense against DoS attacks. Tools like Traverse, with its deep-rooted visualization capabilities, can again prove instrumental here.
Supply chain attacks
Supply chain attacks are when hackers target a third-party vendor or partner that provides software or services to a cloud environment. By compromising the vendor or partner, the hackers can gain access to the cloud data and systems of their customers. For example, the SolarWinds attack in 2020 was a supply chain attack that affected many government and private organizations.
Quantum computing threats
These are situations where hackers use quantum computers to break the encryption algorithms that protect cloud data and communications. Quantum computers can solve certain mathematical problems much faster than classical computers, which could make some encryption methods obsolete. For example, quantum computers could potentially decrypt RSA encryption, which is widely used for secure data transmission.
Zero-day exploits
Zero-day exploits are caused by hackers exploiting a security vulnerability in a cloud software or service that has not been discovered or patched by the vendor or developer. The hackers can use malware or other techniques to attack the cloud systems and data before the vendor or developer has a chance to fix the flaw. For example, a zero-day exploit in Microsoft Exchange Server in 2021 allowed hackers to access email accounts and install ransomware on cloud servers
At DiscoverCloud, we offer an umbrella of cloud services heightened by our innovative accelerators – SAP Assist, Traverse, and Trekora. These specialized tools bring efficiency, effectiveness, and transparency to your cloud services, making your cloud journey smoother while helping you avoid these risks.
How it works: Turning Hurdles Into Opportunities With DiscoverCloud’s Security Assessment
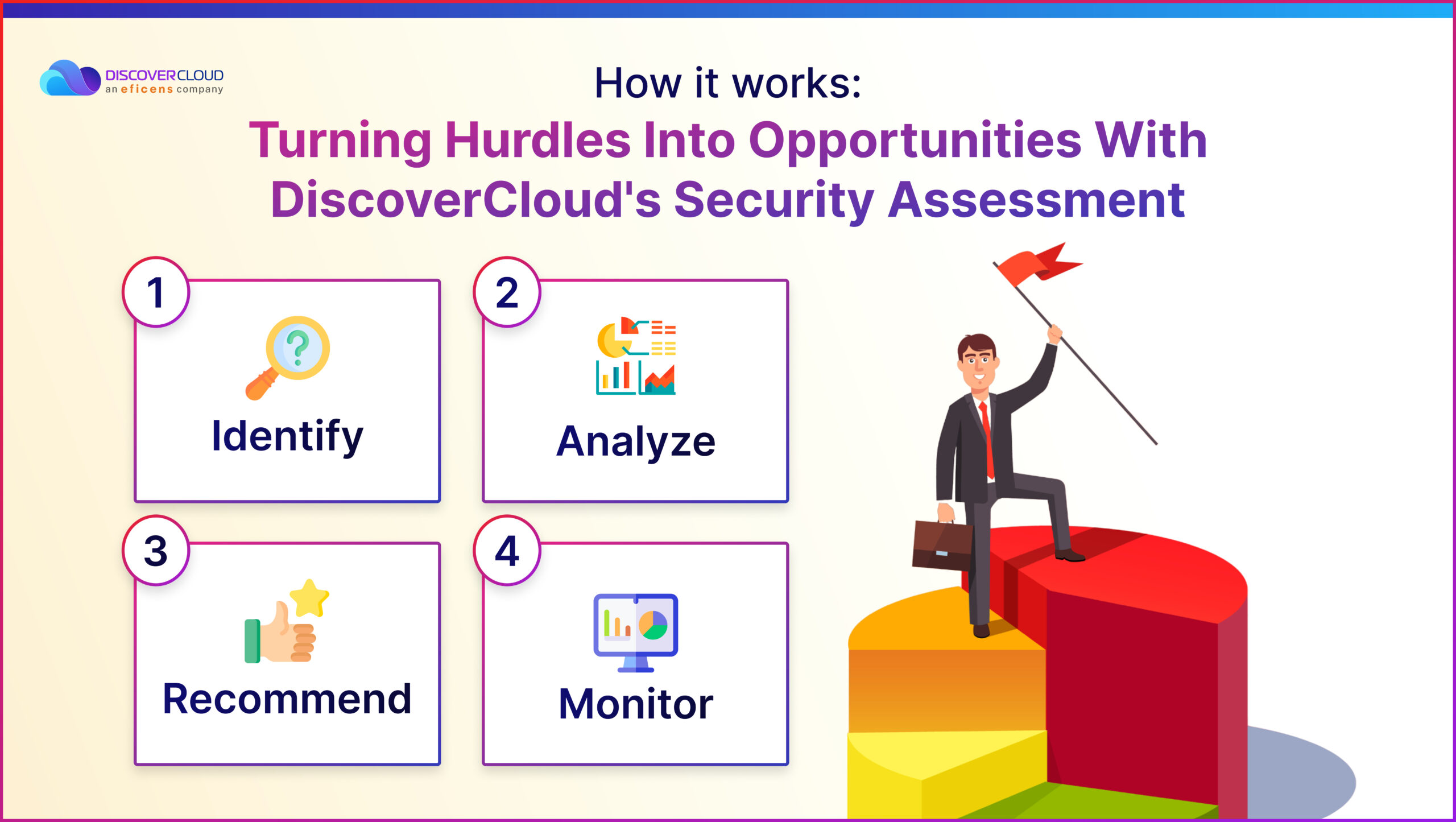
These indeed appear as hurdles but believe it or not, each cloud security risk can be a stepping-stone to improving your cloud environment and building customer trust. Here’s how effective cloud security assessment works, turning threats into opportunities:
- Identify- Identify the cloud assets and resources that need to be protected, such as data, applications, infrastructure, and users. This helps to define the scope and objectives of the assessment.
- Analyze- Study the current state of the cloud environment and the potential threats and vulnerabilities that could compromise its security. This involves using various tools and techniques, such as vulnerability scanning, penetration testing, configuration auditing, and risk assessment.
- Recommend- Suggest the best practices and solutions to mitigate the identified risks and enhance the security posture of the cloud environment. This includes providing guidance on how to implement security controls, policies, standards, and frameworks that align with the business goals and compliance requirements.
- Monitor- Monitor the cloud environment continuously and periodically to ensure that the security measures are effective and up-to-date. This involves using tools and techniques such as log analysis, alerting, incident response, and audit reporting.
The suggestions typically include some best practices and corrections that must be implemented immediately to solve any threats or vulnerabilities, ideally with the help of a cloud expert. Let’s see how that works now.
Best Safety Practices Followed by DiscoverCloud’s SecOps
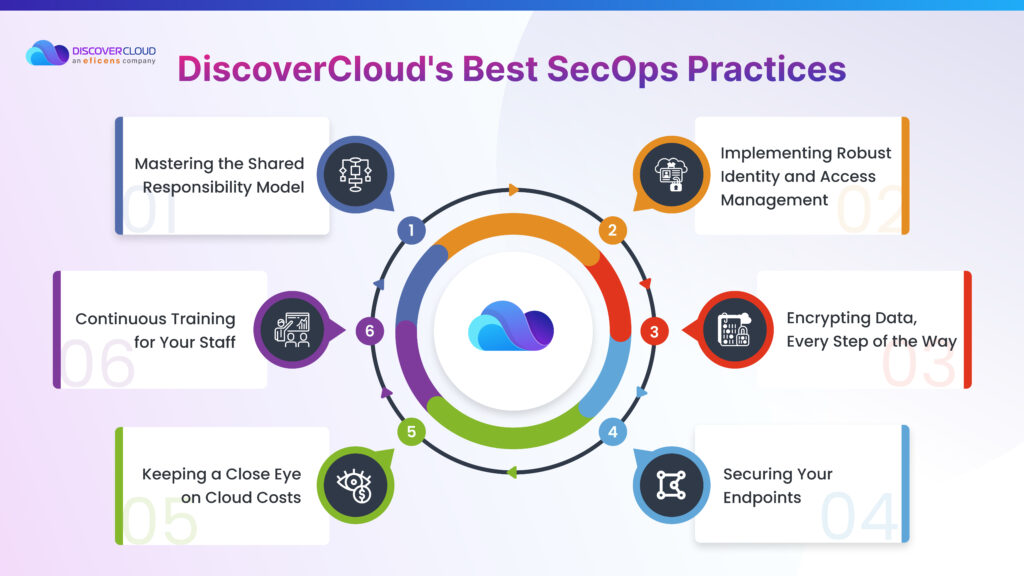
A secure cloud journey is not a destination, but a continuous cycle of evaluation, mitigation, and adaptation. Let’s dive into the best practices you should consider during this process to safeguard your cloud environment from the discussed threats-
Mastering the Shared Responsibility Model
The shared responsibility model is a fundamental tenet of cloud security. It outlines the clear division of labor between cloud service providers (CSPs) and users. Simply put, while CSPs, like AWS or Azure, ensure the security of the cloud, the responsibility for security in the cloud lies with the users. Recognizing this distinction ensures you’re adequately protecting your assets and not leaving gaps expecting them to be filled by someone else.
Implementing Robust Identity and Access Management
It’s crucial to have a solid identity and access management (IAM) mechanism in place. This limits who can access your cloud environments and to what extent. Using a principle of least privilege (PoLP) access model, enabling multi-factor authentication (MFA), and implementing strong password policies are some ways to strengthen your IAM.
Encrypting Data, Every Step of the Way
For optimal data security, encrypt your data at each stage- while at rest, in transit, and in use. Encryption converts your data into an unintelligible format that can only be read or processed after it has been decrypted, offering an additional layer of protection.
Securing Your Endpoints
Cloud security isn’t just confined to data centers. Your endpoints—be it laptops, mobile devices, or IoT devices—provide gateways to your cloud environment and can be susceptible to security vulnerabilities. Having robust endpoint protection and management, coupled with network-level security controls, can safeguard your endpoints from becoming entry points for threats.
Continuous Training for Your Staff
Cloud security isn’t an IT issue alone; it’s an organizational one. Empower your staff with appropriate security knowledge. Regular training will help them recognize common threats, understand the implications of their actions, and ensure they follow the defined security protocols.
Keeping a Close Eye on Cloud Costs
Cloud cost optimization, while not directly a security measure, is an important best practice. It prevents you from overspending on unnecessary or misconfigured resources, thereby helping to allocate budgets more effectively towards mitigating threats.
While these recommendations form a sturdy security foundation, remember that each business’s threat landscape is unique. To truly fortify your cloud environment, assessments should be continuous, and strategies must evolve.
In case you lack full expertise in the area, don’t risk it! You just can’t afford to cut corners on security, and that’s why our experts at DiscoverCloud are here to help you.
The DiscoverCloud Advantage
At DiscoverCloud, we serve as your co-pilot, guiding you safely through your cloud transformation journey. We amplify these security measures using a trifecta of innovative accelerators backed by seasoned cloud service experts. Together, they study every aspect of your cloud environment and help you create simple and safe cloud management procedures:
- SAPAssist– This tool eases SAP migrations with tailored strategies for your business.
- Traverse– This enables workload discovery and visualization, offering a complete overview of your AWS Cloud environment.
- Trekora– Trekora ensures cloud cost optimization and enables transparency in your cloud expenditure.
So, team up with DiscoverCloud for a worry-free cloud journey and safeguard your business in the digital realm. We will provide expert guidance, innovative solutions, and continuous monitoring to ensure your cloud experience is secure, efficient, and cost-effective. And the reward is substantial—operational resilience, business continuity, and customer trust.
Wrapping Up
Cloud security assessment is your digital guardian, a first line of defense that sits between your valuable data and potential cyber threats. It’s not just a layer of security; it’s a proactive approach that keeps your digital environment one step ahead of cybercriminals.
As you embark on the cloud journey, remember to partner with seasoned experts like Eficens DiscoverCloud who will perform security assessments and can steer you clear of potential pitfalls, ensuring a smooth and secure transition. Remember, your cloud’s security is just as vital as its utility. It’s time to rise above the cloud security challenges and harness the unparalleled power of the cloud for your business’s growth and success!